Blogs
I do write about whatever I am learning and doing, mostly about software development. Below are the blogs I have written and I am going to publish more blogs whenever I got some time to write
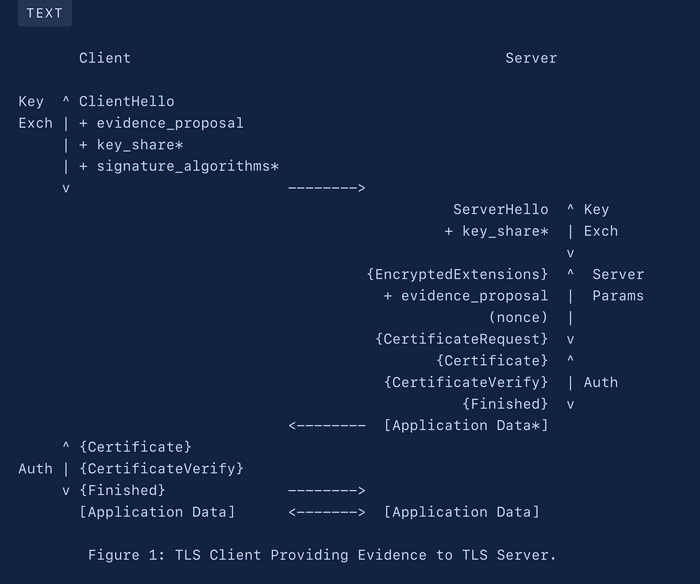
![TLS with Remote Attestation (aTLS) | Machine-to-Machine Secure Channel]()
TLS with Remote Attestation (aTLS) | Machine-to-Machine Secure Channel
An Attested TLS channel is a TLS channel that integrates remote attestation validation as part of the TLS channel establishing process.
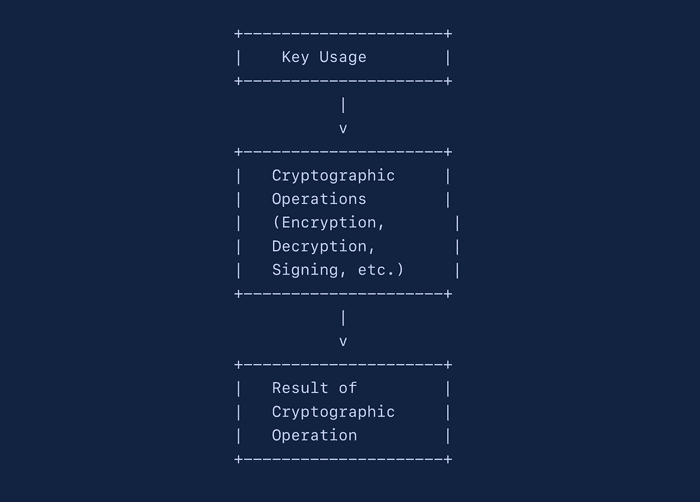
![Managing the cryptographic keys within Trusted Execution Environment]()
Managing the cryptographic keys within Trusted Execution Environment
High level overview of the cryptographic keys management in the Trusted Execution Environment.
![Trusted Platform Module (TPM) as Root of Trust (rot) and cryptographic features]()
Trusted Platform Module (TPM) as Root of Trust (rot) and cryptographic features
High level overview of the trusted platform module its cryptographic features that can be used to perform the platform attestation.
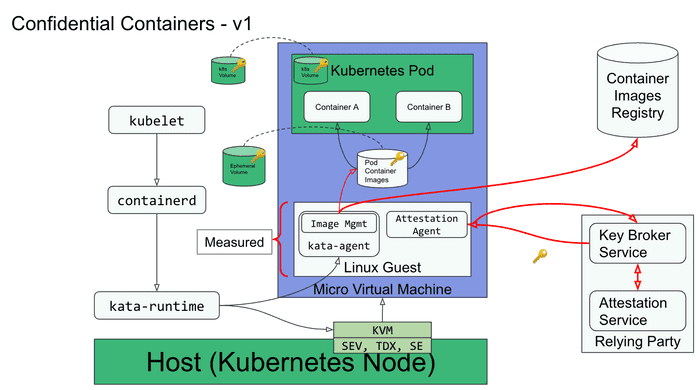
![Deep dive into the Confidential Containers (CoCo)]()
Deep dive into the Confidential Containers (CoCo)
Enabling cloud native confidential computing by leveraging Trusted Execution Environments to protect containers and data
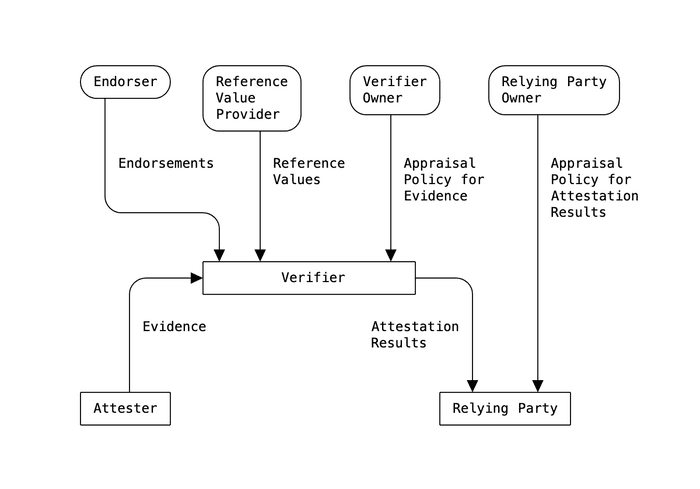
![Remote Attestation Procedures Architecture (RATS) - Part-I]()
Remote Attestation Procedures Architecture (RATS) - Part-I
In this article, we will focus on attestation, as a method to prove specific properties of the system and components being used.
![Protection against vulnerabilities at boot time with Linux Secure Boot Process]()
Protection against vulnerabilities at boot time with Linux Secure Boot Process
Secure Boot is a security feature found in the UEFI standard, designed to add a layer of protection to the pre-boot process
![Bits and pieces of confidential virtual machine architecture]()
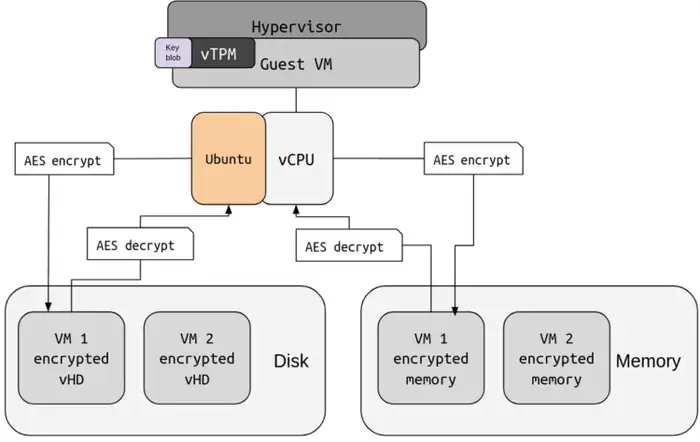
Bits and pieces of confidential virtual machine architecture
In this post, we will look into confidential virtual machines (CVMs) and its core building blocks.
![Zero Trust Architecture and Confidential Computing]()
Zero Trust Architecture and Confidential Computing
How on-chip security features (TEEs) that can significantly boost your Zero Trust solution architecture.
![AMD Secure Encrypted Virtualization (SEV) on AMD EPYC™ Microprocessors]()
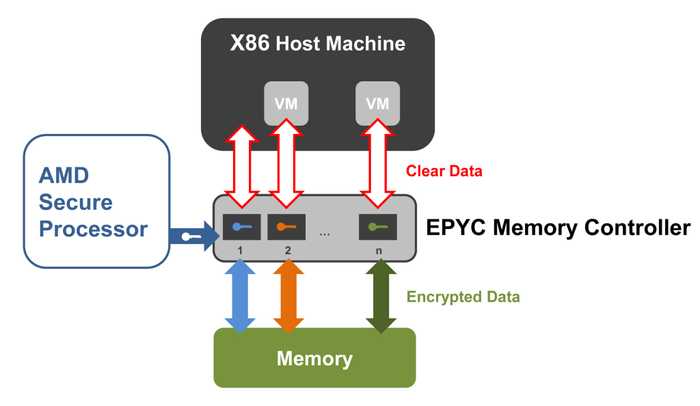
AMD Secure Encrypted Virtualization (SEV) on AMD EPYC™ Microprocessors
Confidential computing on AMD EPYC™ with built-in Encrypted Virtualization (SEV), which helps protect data in use.
![Confidential Compute Architecture(CCA) on Armv9.2+ Microprocessors]()
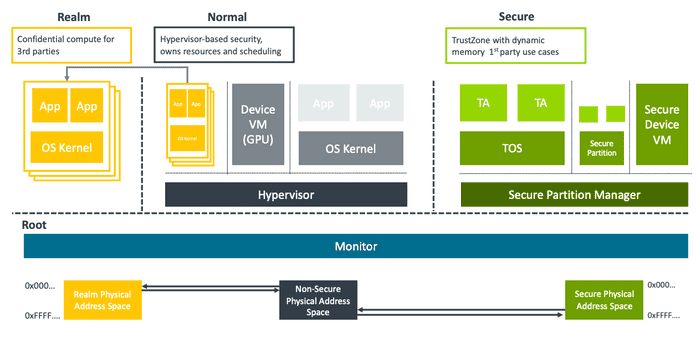
Confidential Compute Architecture(CCA) on Armv9.2+ Microprocessors
CCA is hardware-based secure environment, to shield portions of code and data from access or modification, even from privileged software stack.
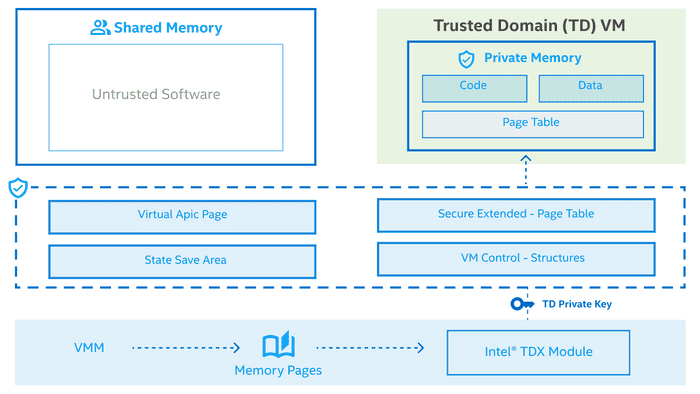
![Confidential Computing on Intel Microprocessors]()
Confidential Computing on Intel Microprocessors
This blog covers the confidential computing (TCB) features on the Intel chips
![Managing Microservice Schema With Protocol Buffers]()
Managing Microservice Schema With Protocol Buffers
Defining the Microservice Schema, Interfaces, Objects, and strategies that can be used to manage Microservice API Interfaces.
![Anatomy of Go-Routines in Go - Golang concurrency pattern]()
Anatomy of Go-Routines in Go - Golang concurrency pattern
Goroutine is lightweight execution thread running in the background.
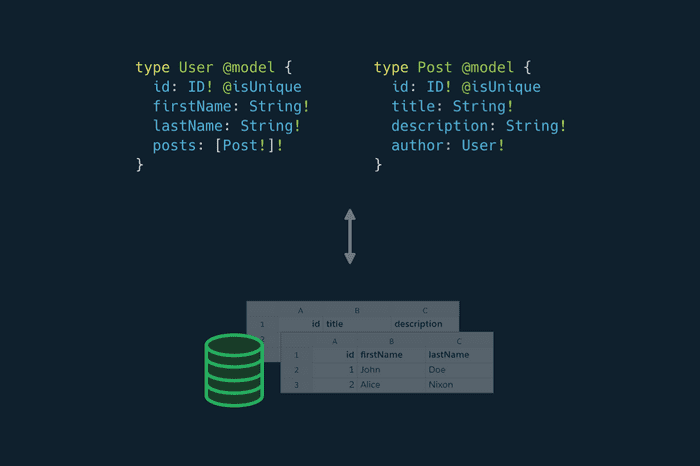
![A Comprehensive Guide to Learn GraphQL & Its Core Concepts]()
A Comprehensive Guide to Learn GraphQL & Its Core Concepts
Tutorial series dedicated to learning the graphql from scratch with examples and working demos
![JWT authentication in Golang with Echo]()
JWT authentication in Golang with Echo
Learn how to build JWT authentication middleware for Echo
![Build Simple API with gRPC, Protocol Buffers in Golang]()
Build Simple API with gRPC, Protocol Buffers in Golang
This guide gets you started with gRPC in Go with a simple working example.